Authentication Type 1 using Active Directory
To configure Transact in a configuration with ADFS over SAML 2.0 with Authentication Type 1 using authentication with Active Directory, follow the instructions in this section.
Authentication with SSO and Active Directory works as follows:
-
Transact only provides authentication details to the Identity Provider.
-
Identity provider verifies the validity of the user and sends back acknowledgment as a part of the SAML response.
-
If validation is successful, the selected authorization method is taken into consideration. If the user connection is set to value 1, authorization uses Active Directory.
-
User name received as the response is matched with the groups and roles fetched from Active Directory.
-
This role matches with user.super_admin property in application.properties. If the match is good, the user is provided with super admin access. Otherwise, the user gets access based on the roles defined in the Access Manager.
Prerequisites
This configuration requires the following to be installed.
-
Active Directory Federation Services
-
Active Directory
-
Ephesoft Transact
You also need to configure the files as shown in Authentication Type 1 on Apache Tomcat, especially the following files:
-
server.xml
-
user-connectivity.properties
-
application.properties
Components
The following components require additional configuration to support ADFS over SAML 2.0 with Authentication Type 1 using authentication with Active Directory.
- Server.xml
-
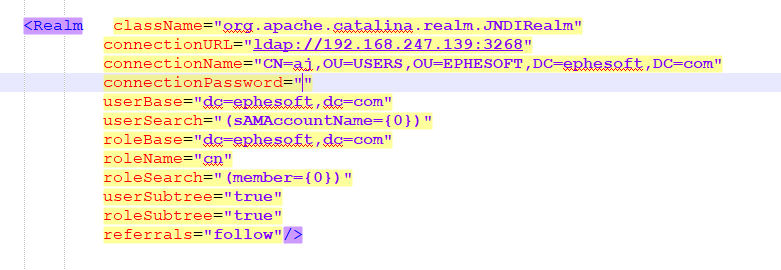
Add the <Realm> configuration for Active Directory as shown below.
Note the following:
-
You also need to change the connectionURL, connectionName, connectionPassword, userBase, roleBase properties to match your Active Directory configuration.
-
Download the sample server.xml from here.
-
- user-connectivity.properties
-
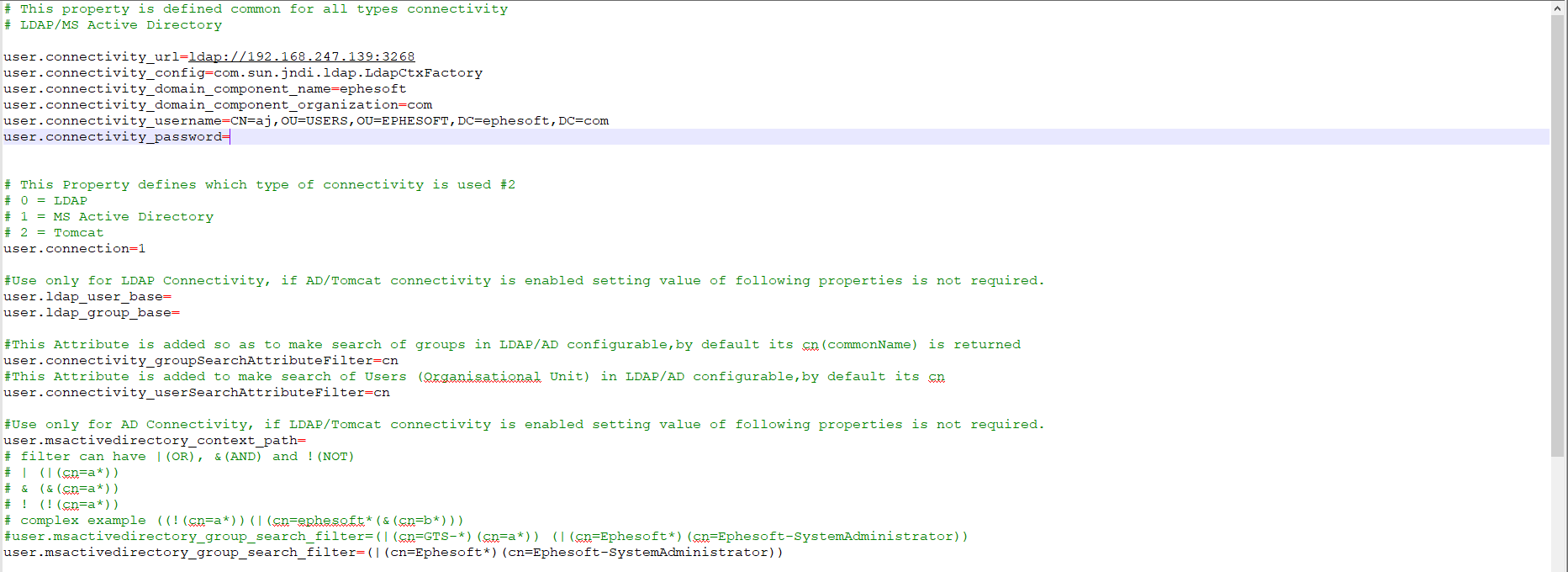
Make the required changes to user-connectivity.properties as shown below.
Note the following:
-
Change the properties as per your Active Directory structure.
-
Download the sample user-connectivity.properties from here.
-
- application.properties
-
This file is used to define Super Admin Group Names. The following properties need to be changed:
-
user.super_admin: Define super admin groups.
-
update_super_admin_group: Change the flag to true.
-
