Configure CAS-based SSO mechanism
The following files must be configured. These are located in the Transact installation folder.
-
\JavaAppServer\conf\server.xml
-
\Application\applicationContext.xml
-
\Application\WEB-INF\classes\META_INF\CAS-config\cas-config.properties
-
\Application\WEB-INF\web.xml
server.xml
To integrate CAS, Transact must be run over SSL with the following suggested configurations:
-
Uncomment the connector protocol. A sample Tomcat connector with suggested configurations is shown below:
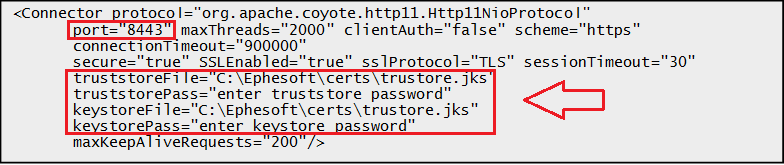
- Provide the keystore file path and its password (if using proxy setup).
-
Provide the truststore file path and password.
Make sure the truststore file is the same as that of %JAVA_HOME% because CAS internally looks for the truststore in the %JAVA_HOME%/jre/lib/security folder.
- Specify the port number (the suggested port is 8443).
- Comment out any other connector, if required.
applicationContext.xml
In the applicationContext.xml file, uncomment either of the following beans based on how you plan to configure CAS SSO:
-
Uncomment the applicationContext-securityCASwithProxy.xml bean in applicationContext.xml to enable CAS SSO with proxy support.
-
Uncomment the applicationContext-securityCASwithoutProxy.xml bean in applicationContext.xml to enable CAS SSO without proxy support.
cas-config.properties
Provide values for cas.server.host and cas.service.host in the properties file. These host addresses are further used to calculate the required URLs and to ensure proper communication between the CAS server and Transact. Transact recommends using port number 8443.
-
cas.server.host represents the complete host address of the CAS server. Example:
cas.server.host=casServer:8443 -
cas.service.host represents the complete host address of the system where Transact is running. Example:
cas.service.host=casServer:8443
web.xml
Modify web.xml as follows:
- Uncomment the characterEncodingFilter filter and its filter mapping.
- Uncomment the springSecurityFilterChain filter and its filter mapping.
- Comment out the sessionTimeoutFilter and its filter mapping.
- Comment out the SessionTimeoutServlet and its servlet mapping.
- Comment out all security-constraint and login-config nodes.
- Change the port to 8443.
- Change the protocol to https.
- Specify 1 as the value for authenticationType.
Truststore and keystore
A Java Key Store (JKS) is a repository of security certificates. CAS exchanges involve usage of cryptography for signing and encryption of data. This Key Store will contain a certificate and private key that will be used to digitally sign CAS messages and encrypt their content.
The CAS server and CAS client (Transact) interact with each other in an encrypted environment. For that purpose, the CAS server and Ephesoft Transact both maintain their own keystore and truststore. The certificate in the CAS server's keystore must be imported into the Transact truststore.
To use CAS with proxy support, the certificate in the Transact keystore must be imported into the CAS server's truststore.
Create private key
- Open a command line or terminal window and make sure you are in your home directory.
-
Execute the following command:
keytool -genkey -alias tomcat -keyalg RSA -validity 365The validity parameter allows you to specify (number of days) how long the certificate should be valid for. The longer the time-period, the less likely you are to need to recreate it. To recreate it, you'd need to delete the old one and then follow these instructions again.The response looks something like this:
Enter keystore password: Re-enter new password: What is your first and last name? [Unknown]: $REPLACE_WITH_FULL_MACHINE_NAME What is the name of your organizational unit? [Unknown]: Test What is the name of your organization? [Unknown]: Test What is the name of your City or Locality? [Unknown]: Test What is the name of your State or Province? [Unknown]: Test What is the two-letter country code for this unit? [Unknown]: US Is CN=$FULL_MACHINE_NAME, OU=Test, O=Test, L=Test, ST=Test, C=US correct? [no]: yesFor the keystore password, enter changeit. When prompted for the first and last name, you should enter your machine name during development. Enter the rest of the information specific to your organization. After confirming the information you have provided, a keystore will be created and a private key will be added to that keystore.
Any application that needs to securely connect to this CAS server must import the certificate. You can export a certificate that's compatible with other JVM keystores by executing the following command:
keytool -export -alias tomcat -file server.crtThe output looks like this:
Enter keystore password: Certificate stored in file <server.crt>You can then import the server.crt into the Transact JVM keystore by executing the following command:
keytool -import -file server.crt -keystore $JAVA_HOME/jre/lib/security/cacerts -alias tomcatThe path of this newly created keystore will be used in configuring the CAS server using Tomcat.
For using CAS with proxy support, perform the following procedure in Transact to create a keystore and import Transact's certificate into the CAS server truststore.
Create private key
- Open a command line or terminal window and make sure you are in your home directory.
-
Execute the following command:
keytool -genkey -alias tomcat -keyalg RSA -validity 365The response looks something like this:
Enter keystore password: Re-enter new password: What is your first and last name? [Unknown]: $REPLACE_WITH_FULL_MACHINE_NAME What is the name of your organizational unit? [Unknown]: Test What is the name of your organization? [Unknown]: Test What is the name of your City or Locality? [Unknown]: Test What is the name of your State or Province? [Unknown]: Test What is the two-letter country code for this unit? [Unknown]: US Is CN=$FULL_MACHINE_NAME, OU=Test, O=Test, L=Test, ST=Test, C=US correct? [no]: yesFor the keystore password, you should enter changeit. When prompted for the first and last name, you should enter your machine name during development. Enter the rest of the information as it applies to your organization. After confirming all the entries, a keystore will be created and a private key will be added to that keystore.
Any application that needs to securely connect to Transact must import the certificate. You can export a certificate that's compatible with other JVM keystores by executing the following command:
keytool -export -alias tomcat -file server.crtYou will get output that looks like this:
Enter keystore password: Certificate stored in file <server.crt>You can then import the server.crt into the CAS JVM keystores by executing a command like this:
keytool -import -file server.crt -keystore $JAVA_HOME/jre/lib/security/cacerts -alias tomcat - Restart the Transact server.
